DetectAI: Licensed Media Detection &
Policy-Grade Enforcement
Why Now?
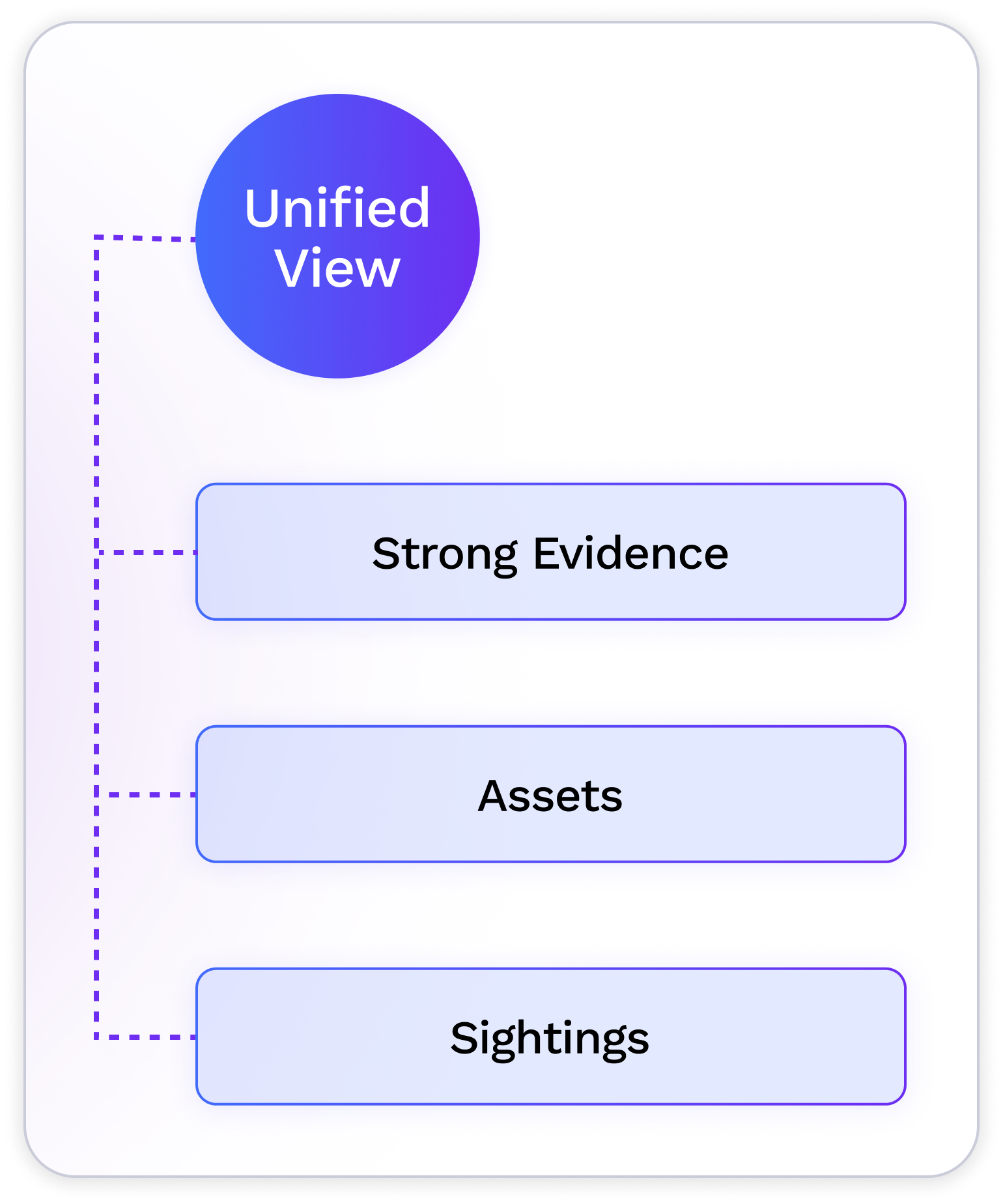
Platforms strip metadata, AI blurs provenance, and single-signal tools miss edited or derivative media. Rights teams need a unified, trusted view of where assets appear, which sightings break policy, and evidence strong enough for takedowns and recovery.

What DetectAI Does
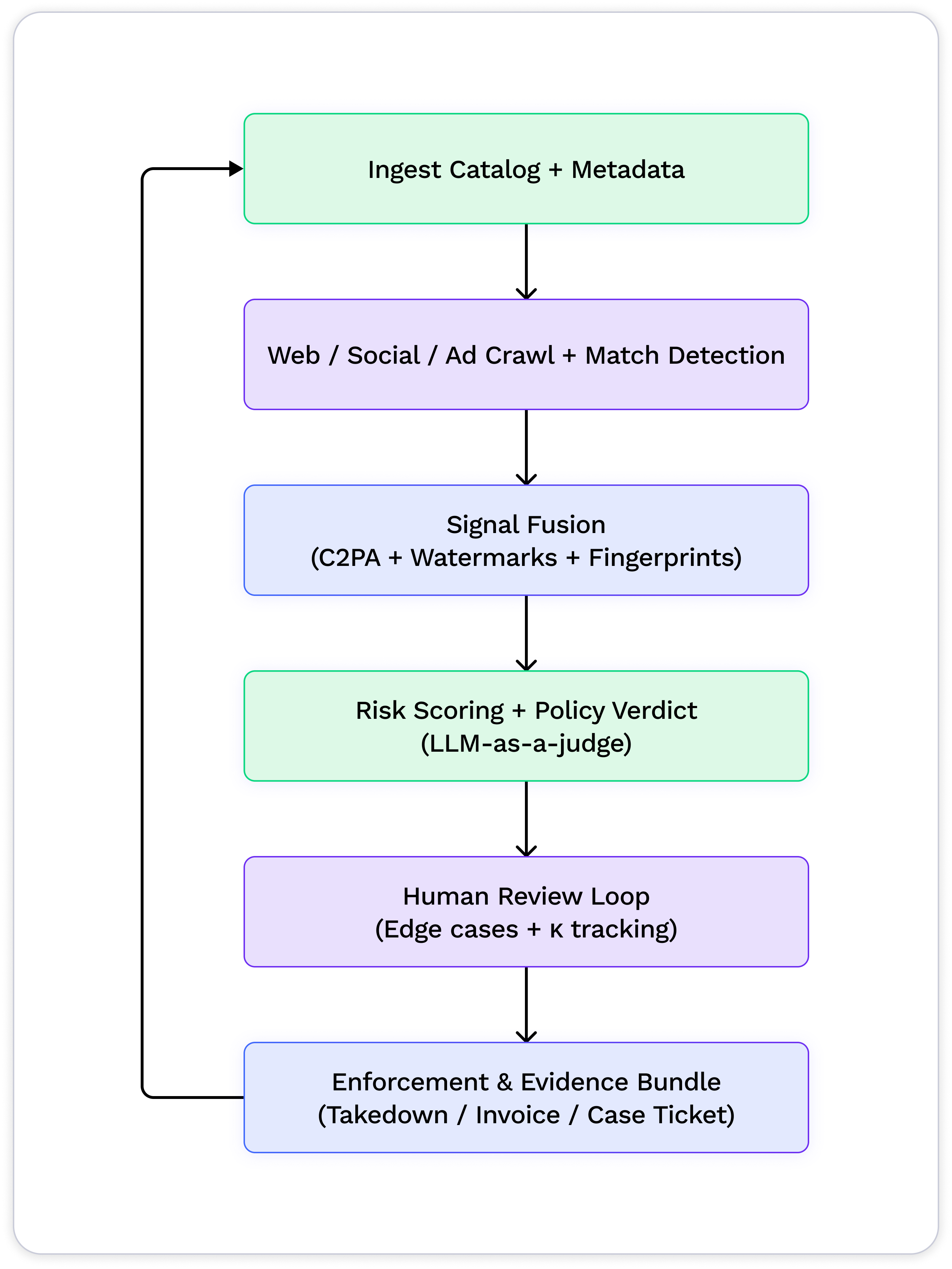
1. Ingest your reference catalog & license metadata.
2. Search across web, social, and ad networks for matches, including cropped, recolored, or re-encoded variants.
3. Fuse multiple authenticity signals (C2PA, visible/invisible/model watermarks, perceptual fingerprints, telemetry).
4. Score each sighting with a calibrated risk + policy-violation verdict (LLM-as-a-judge with guardrails).
5. Escalate edge cases to expert reviewers; track κ and overturns to keep calibration honest.
6. Deliver evidence bundles (hashes, manifests, logs, screenshots) and trigger takedowns, invoices, or case tickets via API/webhooks.
Built for “Policy Violation” Work
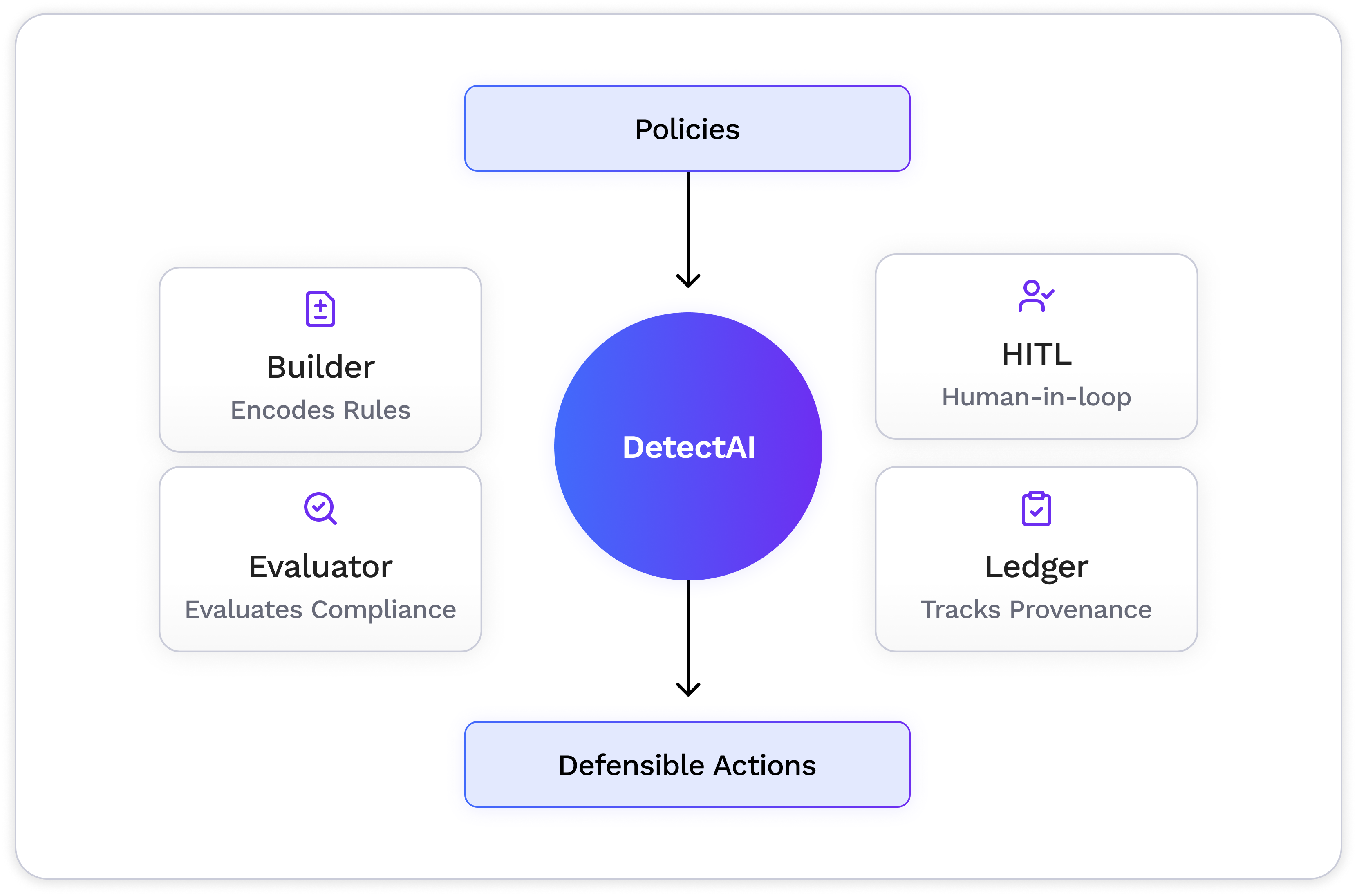
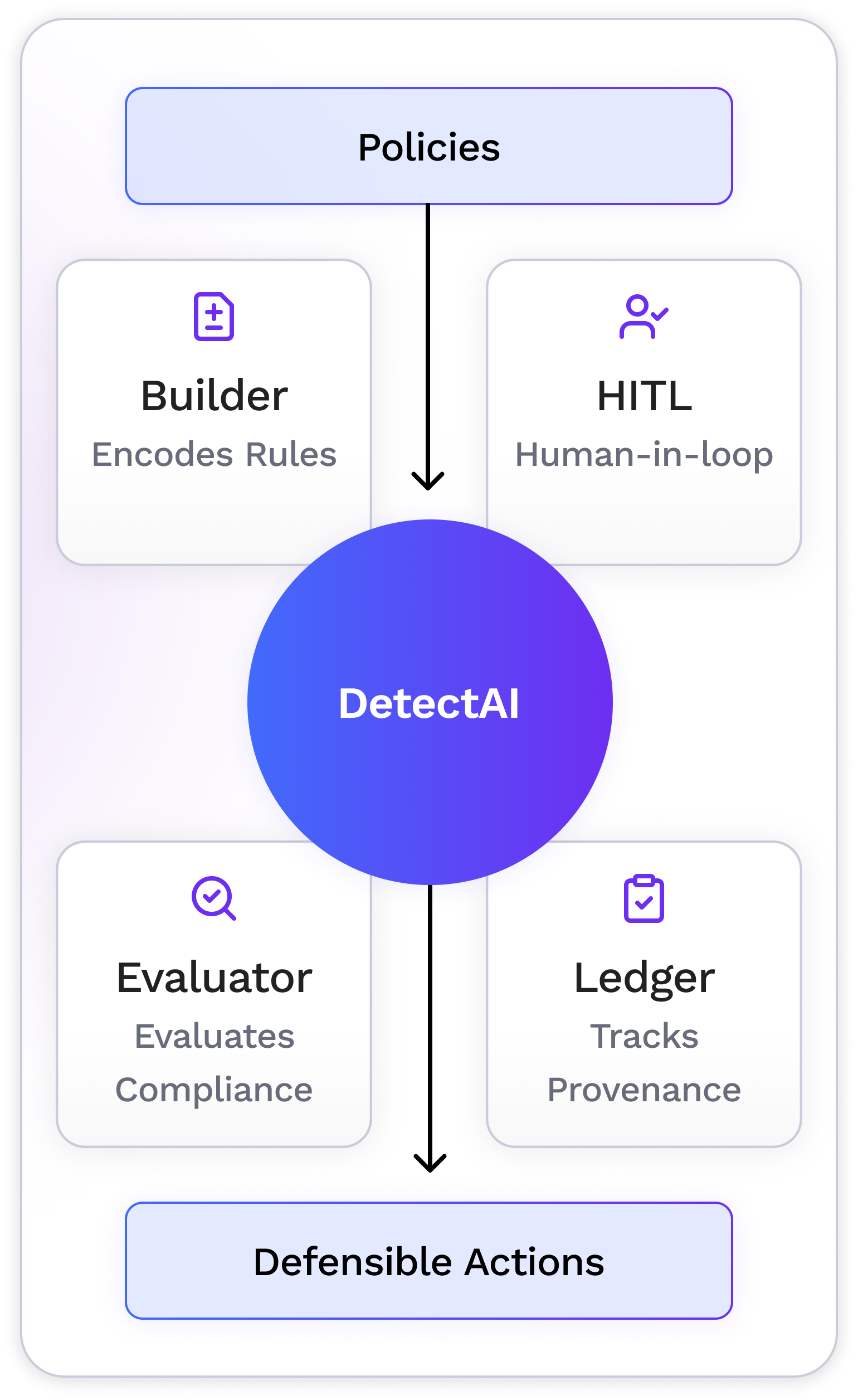
We’re policy-to-enforcement veterans. Our platform encodes your licensing terms, usage rights, and partner policies as machine-enforceable rules, then backs every decision with defensible artifacts and human-in-the-loop confirmation when needed. Our platform modules (HITL workbench, evaluator, policy & taxonomy builder, data provenance ledger) are safety-grade.
Why TrustLab?

Multi-signal > Single-signal
DetectAI reliably handles transformed media (crop, recolor, re-encode) by fusing C2PA, watermarks, fingerprints, and telemetry instead of relying on brittle hashes.

Evidence that Stands Up
We deliver chain-of-custody bundles with cryptographically verifiable elements and consistent formatting for claims, takedowns, and invoices.

HITL Where It Matters
Gray-zone detections route to expert reviewers with calibration targets (e.g., κ ≥ 0.75; overturn % monitored) so you can trust the calls.

Battle-tested LLM-as-a-Judge
We operationalize LLM evaluators as scalable, application-specific judges: binary criteria, low temperature, structured outputs, and “explain-why” rationales, aligned to human labels and refreshed over time. (Why this works and best practices.)

No-drama Integration
Modular APIs let you start C2PA-only, fingerprint-only, or full fusion; egress to Rightsline, Salesforce, DAM/CMS, SIEM and more.

Security by Default
PII redaction at ingest, hashed identifiers for provenance data, SOC 2/ISO alignment, SSO/SCIM, and on-prem options for sensitive catalogs.
Boost Your Licensing Revenue Drivers
Recall (top-K match)
≥ 90%
False Positive Rate
≤ 5%
Mean Time to Detection
≤ 6 hours from sighting → alert
Evidence Completeness
95% of cases include full provenance + logs
Reviewer Agreement
0.75 on gray cases
How DetectAI Works
Ingress
Reference catalogs + license DBs; live crawls; partner feeds (CDN/ad networks); EXIF/C2PA manifests; watermark/fingerprint extractors.
Decisioning
A prompt schema fuses signal features; scores are calibrated (e.g., Brier/ECE) and thresholded for high recall on known assets at low FPR. LLM-as-a-judge applies policy rubrics with JSON verdicts and rationales.
HITL
Risk-tiered queues, adjudication, κ tracking, and dispute workflows ensure consistency and reduce false actions.
Egress
Webhooks/API into rights systems, DAM/CMS, CRMs, and ticketing to automate takedowns, invoices, and case creation, plus exportable evidence PDFs/JSON.

Where DetectAI Shines
Stock Libraries &
Studios

Find and prioritize high-value unlicensed use; ship invoice + evidence.
Sports & Labels
Track derivative clips and remixes across social; escalate borderline “fair use” to experts.
Newsrooms

Verify authenticity and lineage pre-publication; flag synthetic or manipulated assets.
Independent Creators &
Agencies

Protect flagship campaigns; centralize violations and takedowns.
What You Get on Day 1

Quickstart Run
Quickstart run on a pilot catalog (connectors + first detections).

Policy Mapping Workshop
Policy mapping workshop to encode your license rules.
Live Dashboard
Live dashboard with risk-ranked sightings and exportable evidence.

API Key & Integrations
API keys & integrations to your existing rights ops stack.
Plan Options
Pilot

Multi-signal detection

Dashboard

Evidence export

Check Our Performance based on a Free Pilot
Pro

HITL workbench

Adjudication metrics

Advanced integrations
Enterprise

Custom Policies

Enhanced SLAs

Dedicated Support
Frequently Asked Questions
SOC 2/ISO posture, PII redaction, hashed identifiers, private networking, and regional processing options are standard.
Yes. DetectAI doesn’t rely on a single signal: perceptual fingerprints + telemetry + residual provenance catch edits and reposts even when EXIF/C2PA is absent.
Used properly, as focused classifiers with binary labels, examples, low temperature, and periodic human reconciliation, LLM judges approximate human judgment and scale continuous monitoring. We follow published best practices and maintain alignment to your rubrics.
We optimize for high recall with low FPR, then route ambiguous cases to trained reviewers. We track κ and overturn rates, and we version policies to avoid drift.
Tell Us Your Top There Assets to Protect
We'll run a targeted crawl, return risk-ranked sightings with evidence, and map the ROI from faster enforcement and recovered licensing value. Let's talk.




